UPDATE – 20 May 2020 at 7:45 PM
SUMMARY
It’s time to update your iPhone and iPad devices (found in Settings > General > Software Update) and then enable the Mail program for your various accounts (found in Settings > Passwords & Accounts).
MORE DETAILS
Apple has released an update to replace iOS 3.4.1 with iOS 3.5, unexpectedly skipping several expected updates and taking the operating system directly to a version that was until recently only available as a non-public BETA version.
Apple updates almost always include mention of security patches and enhancements. This update oddly contains no mention of security improvements. This is unexpected since it’s know that there were serious security problems discussed over two months in communications between Apple and the security firm ZecOps. The serious problems were fixed by Apple in version 3.5 of the BETA (non-public) version of the iOS iPhone / iPad operating system.
It’s likely that Apple was advised by their in-house legal team to admit nothing regarding the security vulnerability since numerous individuals and companies had reportedly impacted by the vulnerability. The presence of the security flaw over 10 years, Apple’s seeming lack of awareness about it, and their delay of about a month to address the issue could make them the target of a class-action lawsuit for their inaction.
According to an article posted today by Mashable: “Notably, Apple’s security updates page doesn’t list iOS 13.5 as patching any security vulnerabilities. However, in general it’s good practice to always keep your devices up to date.”
For those who have been following this developing story over the past month, today’s announcement is a relief. It’s disappointing that Apple has made no public statements about the security issue.
UPDATE – 20 May 2020 at 2:28 PM
As of 20 May 2020, there continues to be no security update from Apple and seemingly no public response. Delays and lack of responsiveness can be embarrassing for security firms because it implies that the issues they’ve identified are unsubstantiated and irrelevant, or incorrect.
Even when security issues exist, companies like Apple will sometimes ignore vulnerabilities and delay updates to convey to the public that there was no security problem, everything is under control, and they don’t need any third-party security teams helping them to find vulnerabilities in their products.
The latest follow-up report from ZecOps provides additional information about this security vulnerability and poses the following pointed questions to Apple:
- How many triggers have you seen to this heap overflow since iOS 3.1.3?
- How were you able to determine within one day that all of the triggers to this bug were not malicious and did you actually go over each event ?
- When are you planning to patch this vulnerability?
- What are you going to do about enhancing forensics on mobile devices?
Further ZecOps research has identified this problem was present over the past 10 years.
While Apple provides good devices and software, their responsiveness to customer usability and security concerns is notoriously slow. A visit to the online user community discussion forums will reveal that there are many customer complaints that are wide-spread over long periods of time that don’t get a timely response or resolution. For more about this phenomenon, read “Apple’s Slow and Careful Crisis Management Doesn’t Always Work” from 2011.
UPDATE – 9 May 2020
As of 9 May 2020, Apple has still not released updates for their iPhone and iPad iOS-based devices. You can check for the update on your own by going to Settings > General > Software Update. When the update becomes available you will see a notification there.
SUMMARY – 24 April 2020
In the past 24-48 hours, news has spread of a malicious virus that can potentially take control of the more than 1.5 billion Apple iPhone and iPad devices around the world. This document addresses what the problem is and what action you can take to protect your devices.
This is just one example of many recently that are part of a world-wide effort by hackers and fraudsters to capitalize on the disruption of the current world-wide pandemic which is making people less attentive and prepared. So, be alert to email scams, viruses, fake pop-up messages, and other attempts to disrupt your life.
Five Action Criteria
There are so many ongoing reports of security vulnerabilities, malware threats, and scams. A person could spend many hours responding to each one. So, how do we know which ones we should take action on? Here are three simple criteria:
- Exposure Risk. How likely is it that you will be exposed to the threat? Low or high?
- Remedy Cost. How much time and/or money is required to avoid the risk. Low or high cost?
- Threat Impact. What is the impact of the threat? Is it simply an annoyance or does it expose you to greater harm? Low impact or high impact?
- Ease of Implementation. How easy is is it for hackers to gain access to the tools? Some methods of hacking are complicated, costly, or difficult to implement. Others are easy. If the tools are high cost, then it’s less likely to be implemented.
- Delivery Method. Some hacking techniques require control over network equipment like routers, and then victims need to click on some link, download something, or install something before the hacker can take control. Other mechanisms require very little effort on the part of the hacker and little or no action on the part of the victim.
If several of the above factors are high, then it’s likely a person should take action.
With the Apple iOS Mail vulnerability, the exposure risk at present seems to be low, but it could easily spread rapidly with little warning. The remedy cost is very low. Flip a switch and you are protected. The threat impact is high and could result in loss of data or extortion scams. The ease of implementation and delivery method are simple.
Given that the potential harm is great and the remedy takes little effort, it is a good idea to take action on this threat.
Background
Apparently the Apple Mail security vulnerability has been present for 8 years, and is believed to have been exploited since at least 2018. Now that it’s in the news, attempts to exploit the vulnerability will be on the rise.
Update Expected
Apple may release a security update in a few weeks or sooner, but until then hackers will be working around the clock to harm as many people as possible. The problem impacts everyone with iPhone and iPad operating systems from iOS 6 to 13.4.1 versions and everything in between for the past 8 years.
Take Action Now
Until Apple releases an update beyond the current 13.4.1 version of iOS, follow the steps outlined below.
STEP 1 – Disable Mail
Some articles suggest you should completely remove the mail program from your device to avoid having it running in the background. This could result in you having to setup and configure all of your mail accounts later. A more convenient solution is to disable the Mail program instead of removing it. Follow these instructions to disable mail.
- Settings. Go to Settings on your device.
- Passwords & Accounts. Scroll down in Settings and tap on Passwords & Accounts.
- Select Account. You will see one or more accounts listed. Tap on an account to view the features that are enabled for that account such as Contacts, Calendars, Reminders, Notes, and Mail.
- Disable Mail. Touch the on/off slider switch to turn off mail for each of your accounts. This will preserve the account setup and login information for later when you need to turn it back on. Below you can see an example of the screen you will see. You want to make sure the Mail switch does not show green (on) but instead is gray (off) which happens when you slide the switch left. The example below is for a Gmail account. Other services may show different options than what is shown below.
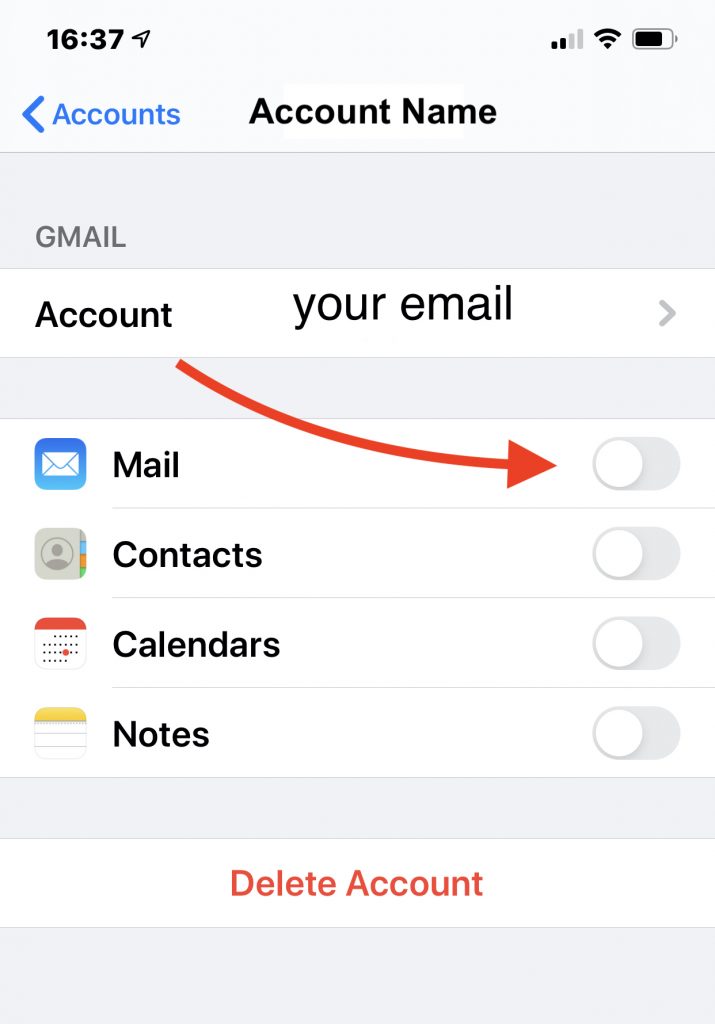
With the Apple Mail App disabled, you won’t receive any emails, legitimate or malicious ones, and tapping on the Mail app will just present an account setup screen. With no emails being received by the program, you should be safe.
STEP 2 – Choose an Email Program
For those who are staying at home and/or don’t plan to need email access while mobile, you need not continue with the remaining steps and suggestions, but you might want to read them anyway.
Two email apps for iPhone and iPad commonly suggested are Microsoft Outlook and Gmail. However, those two have some limitations. Here are some suggestions and considerations for deciding what email solution could work well for you.
- Browser. You could use your web browser to access email through your service provider’s website. This works on iPhone and iPad devices, and it’s something you can do immediately with no further configuration.
- Edison Email. The Edison Email app works with many different email services and its key feature is that it will allow you to use your existing iPhone or iPad Contacts app.
- GMail. The Gmail app works okay for existing Gmail users who have no other email service they need to check. However, there is no built-in contacts feature and no ability to access the Contacts in your device. For names in your Google Contacts list, email addresses are automatically filled in as you type someone’s name. If you need to access your Gmail contacts list you will need to go to https://contacts.google.com which makes the email software difficult to use.
- Outlook. The Microsoft Outlook app has a Calendar function, but lacks the other familiar features of the desktop and web versions of Outlook such as the ability to easily work with contacts. There’s an odd magnifying glass icon that gives you the ability to search for contacts but that contacts feature doesn’t integrate with the iPhone contacts and won’t synchronize with your Google contacts, all of which renders the Outlook program kind of useless.
Given the above considerations, the browser or the Edison Email app will work best for most people.
STEP 3 – Install Edison Email
As mentioned in STEP 2, a good alternative to the Apple Mail program is the Edison Email app. If you feel it’s a good choice for you, follow these instructions to install and configure the app.
- Go to the App Store on your device.
- Search for Edison Email in the App Store.
- Click on the Get button. Or, if you’ve downloaded the app previously, you may see a cloud with a down arrow indicating you can download it again. If the app is already installed, instead of seeing a Get button you will see an Open button.
- When you first open Edison Mail you’ll be prompted to allow access to your Contacts for the program to be able to address emails to people. You can confirm that and continue.
- To setup an account, simply enter your email address and provide the password to access your email.
You can add another account, or go directly to your inbox. To access contacts, use the Contacts app on your device as you always have for editing, adding, or deleting contacts.
STEP 4 – Check Back
In a few weeks or less, your iPhone or iPad should receive a notification under Settings > General > Software Update, indicating that an update to iOS 13.4.2 or perhaps 13.4.5 is available. It isn’t known at present what the new version number will be, or when it will be released, but once your phone is updated, and the Apple Mail program is secure, you will probably want to go back and activate mail again. You can do so by going to STEP 1 described above and enabling Mail in your accounts again.
Future Relevant Information
This document will be updated with further news as it becomes available, so feel free to check back later.
Further Reading
Here are some links to learn more about this issue.
- 9to5Mac, 22 Apr 2020 at 8:15 AM CT. “Report: iPhone Mail app zero-day exploits found in the wild, Apple has fix coming in next public iOS release” Excerpt: “A new potentially serious software vulnerability has been discovered in iOS 13 that works via the default Mail app on iPhone and iPad. The security group ZecOps (via Motherboard) says that one of the two vulnerabilities is a zero-click exploit (no user interaction needed) that can be performed remotely.” [More]
- Ars Technica, 22 Apr 2020 at 3:19 PM CT. “A critical iPhone and iPad bug that lurked for 8 years may be under active attack” Excerpt: “A critical bug that has lurked in iPhones and iPads for eight years appears to be under active attack by sophisticated hackers to hack the devices of high-profile targets, a security firm reported on Wednesday. The exploit is triggered by sending booby-trapped emails that, in some cases, require no interaction at all and, in other cases, require only that a user open the message…” [More]
- Forbes, 23 Apr 2020. “Apple Confirms New Warning Affecting Almost All iPhone Users” Excerpt: “Apple has … just confirmed a massive iOS security hole which impacts almost every iPhone on the planet. … Apple claims 1.5 billion active devices of which iPhones make up the majority…” [More]
- ZecOps, 20 Apr 2020. “You’ve Got (0-click) Mail!” Excerpt: “Following a routine iOS Digital Forensics and Incident Response (DFIR) investigation, ZecOps found a number of suspicious events that affecting the default Mail application on iOS dating as far back as Jan 2018. ZecOps analyzed these events and discovered an exploitable vulnerability affecting Apple’s iPhones and iPads. ZecOps detected multiple triggers in the wild to this vulnerability on enterprise users, VIPs, and MSSPs, over a prolonged period of time. The attack’s scope consists of sending a specially crafted email to a victim’s mailbox enabling it to trigger the vulnerability in the context of iOS MobileMail application on iOS 12 or maild on iOS 13. Based on ZecOps Research and Threat Intelligence, we surmise with high confidence that these vulnerabilities – in particular, the remote heap overflow – are widely exploited in the wild in targeted attacks by an advanced threat operator(s).” [More]
